The OAuth 2.0 authorization framework enables a third-party client app to gain limited access to a user's protected resources without the need for the user to divulge their login credentials to the app. An authorization grant gives the app permission to retrieve an access token on behalf of the end user. OAuth 2.0 supports four different grant types that each have different flows to gain an access token.
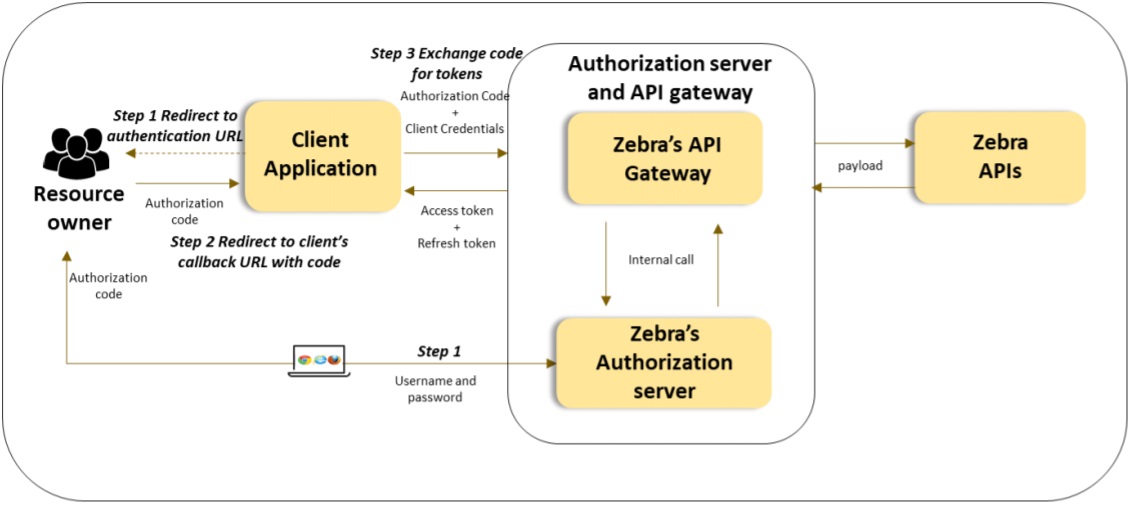
Authorization Code is considered the most secure OAuth 2.0 grant type. Before the authorization server issues an access token, the app must first receive an authorization code from the resource server.
After successfully logging in to the resource server, the app will receive an authorization code that it can use to negotiate an access token with the authorization server. Typically, this grant type is used when the app resides on a server rather than on the client. This grant type is considered highly secure because the client app never handles or sees the user's username or password for the resource server (that is, for example, the app never sees or handles your Twitter credentials). This grant type flow is also called "three-legged" OAuth.
Use CasesThe Authorization Code grant type is appropriate for untrusted apps written by third-party developers who do not have a trusted business relationship with the API provider.
Authorization Grant Type Flow
Getting Started
To use the OAuth APIs, you must first add them to your App in the developer portal.
Pre-requisites
1. The client application developer must register at the Zebra developer portal and obtain a user account login and password.
2. Contact Zebra's service desk to register the client application and redirect URI and obtain a Client ID and Client Secret
Authorization Grant Type Flow

Getting Started
To use the OAuth APIs, you must first add them to your App in the developer portal.
Pre-requisites
1. The client application developer must register at the Zebra developer portal and obtain a user account login and password.
2. Contact Zebra's service desk to register the client application and redirect URI and obtain a Client ID and Client Secret
The OAuth 2.0 authorization framework enables a third-party client app to gain limited access to a user's protected resources without the need for the user to divulge their login credentials to the app. An authorization grant gives the app permission to retrieve an access token on behalf of the end user. OAuth 2.0 supports four different grant types that each have different flows to gain an access token.
Authorization Code is considered the most secure OAuth 2.0 grant type. Before the authorization server issues an access token, the app must first receive an authorization code from the resource server.
After successfully logging in to the resource server, the app will receive an authorization code that it can use to negotiate an access token with the authorization server. Typically, this grant type is used when the app resides on a server rather than on the client. This grant type is considered highly secure because the client app never handles or sees the user's username or password for the resource server (that is, for example, the app never sees or handles your Twitter credentials). This grant type flow is also called "three-legged" OAuth.
Use CasesThe Authorization Code grant type is appropriate for untrusted apps written by third-party developers who do not have a trusted business relationship with the API provider.
Subscribe to email updates
Monthly updates from our Zebra development team, straight to your inbox.
